We shoulder responsibilities for sustainability
by incorporating ESG foundations in our DNA at Ennostar
Information security and privacy controls have become an essential part of business. Our parent company has established a dedicated information security management department responsible for information security maintenance, information security frameworks, information security policies, and other information security projects and review procedures to lead our subsidiaries in joint realization of Ennostar information security goals. The Group has established information security management regulations to ensure normal, secure, and stable operations of core information systems (ERP/MES/CIM) and critical information infrastructure. These regulations serve as the ultimate guideline for information security management systems at our information center, providing secure and trustworthy information services; safeguarding confidentiality, integrity, and availability of information center assets and compliance with relevant regulations; maintaining business continuity; reducing information operation risks; and protecting the rights of information service users. For more information on the Ennostar Group’ s information security policies, please refer to the o icial Ennostar website.
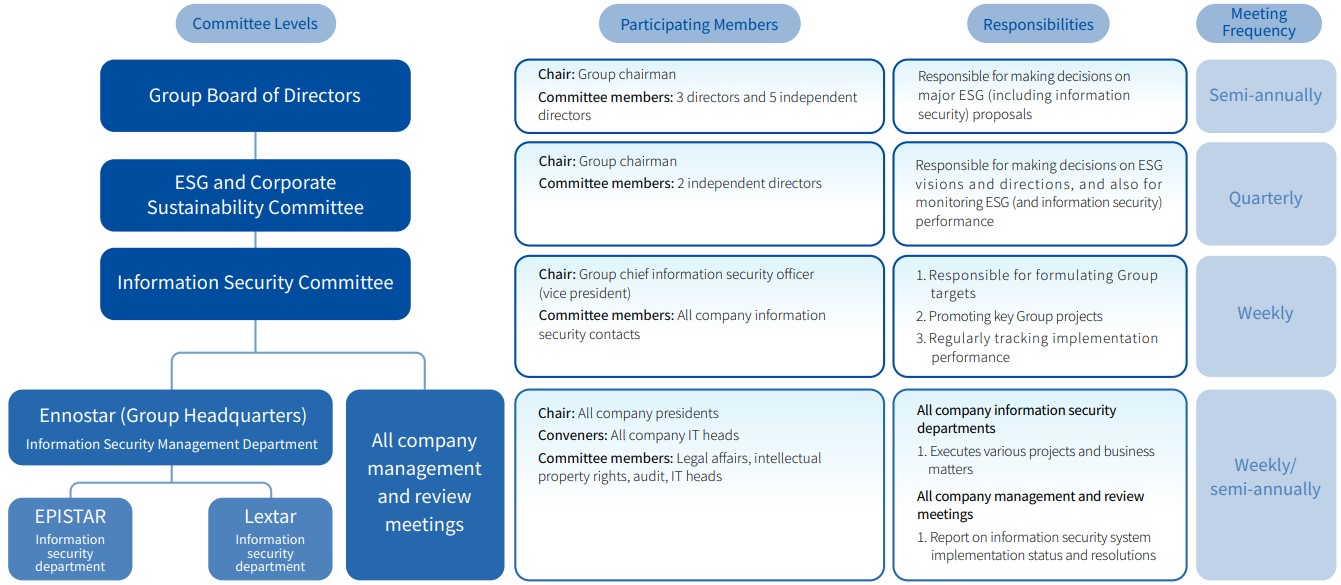
The Group established the “Information Security Committee” to oversee information security implementation strategies, goals, and performance. The Board makes up the first level of our information security framework and is responsible for making decisions on major information security proposals. The Corporate Sustainability and Risk Management Committee (chaired by the Group chairman) makes up the second level of our information security framework and is responsible for determining the Group’ s information security directions and goals. The Information Security Committee (chaired by the chief information security o icer) makes up the third level of our information security framework and is responsible for promoting Group goals and key projects. The information security departments of each subsidiary make up the fourth level of our information security framework and are responsible for implementing various targets and projects. We convene information security management and review meetings twice every year, and report information security implementations and resolutions to the presidents of each.
To ensure information security, achieve the quality expected by our customers, and protect customer privacy, the Group adhered to ISO 27001 requirements in formulating corporate information protection and management processes. In 2024, the Ennostar Group obtained ISO 27001 Information Security System verification for all factories in Taiwan and established information security procedures which comply with international standards. We hope that these international verifications can reduce corporate information security threats, establish the highest standards for protection of confidential information, and protect customer intellectual property rights, process parameters, and other confidential information.
To reduce possibilities and impacts of risk incidents, the Group actively implements management systems and risk response measures:
- Pass external third-party independent ISO 27001 information security audit verifications each year.
- Conduct risk evaluations once every six months.
- Conduct internal audits once every six months.
- Implement daily monitoring to check whether cyberattacks have triggered major information security incidents.
- Conduct 4 non-periodic social engineering and phishing email drills every year.
- Conduct business continuity drills each year in accordance with business process impact analysis charts.
- Ensure that weekly third-party Security Scorecard scores are maintained at A level (90 points or above) and monitor Security Scorecard system every day to check whether there are any new vulnerabilities that should be fixed.
- Regularly monitor and identify vulnerabilities in application programs and third-party packages used by each department, and refer severe and high-risk items to relevant departments for handling. We reference the Common Vulnerability Scoring System (CVSS 3.0) base score metrics to determine vulnerability severity levels, assist departments in conducting security vulnerability testing and patching, and audit patching status.
- Formulate and implement vulnerability scanning plans.
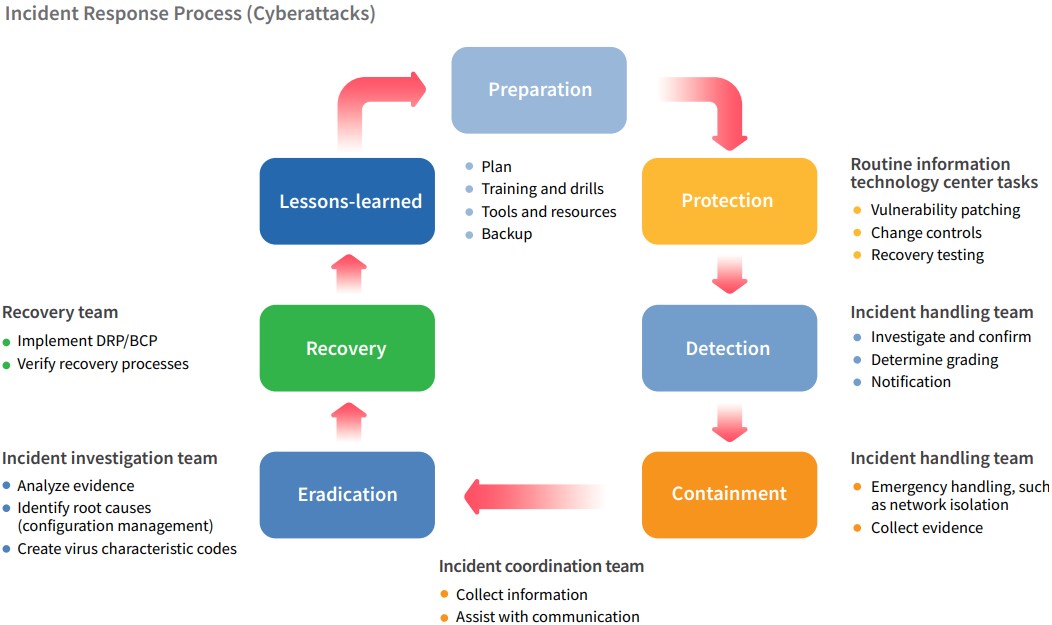
The Group has formulated an incident response mechanism which encompasses seven management processes: prepare, protect, detect, contain, eradicate, recovery, and review. At the prepare level, we comprehensively integrated endpoint detection and response (EDR) tools and third-party monitoring mechanisms for real-time monitoring and response. Apart from routine backups and storage of o line backups, we also implement incident response drills each year in accordance with our response plans. At the protect level, we use vulnerability scanning and third-party risk monitoring platforms to keep informed of vulnerability risks, and report on vulnerability patching progress at weekly meetings. Managers can also conduct restore testing using backups. When information security incidents are detected, we assess incident levels and report said incident, setting containment as our primary goal. We disconnect networks and use other isolation measures to reduce incident impacts, and collect and appropriately store digital evidence to prevent reoccurrence of said incident a er investigation of root causes and eradication of said threat